SOLUTION
AppGuard Enterprise
HOME > SOLUTION > AppGuard > AppGuard Enterprise
“AppGuard Enterprise reduces your operational burden”
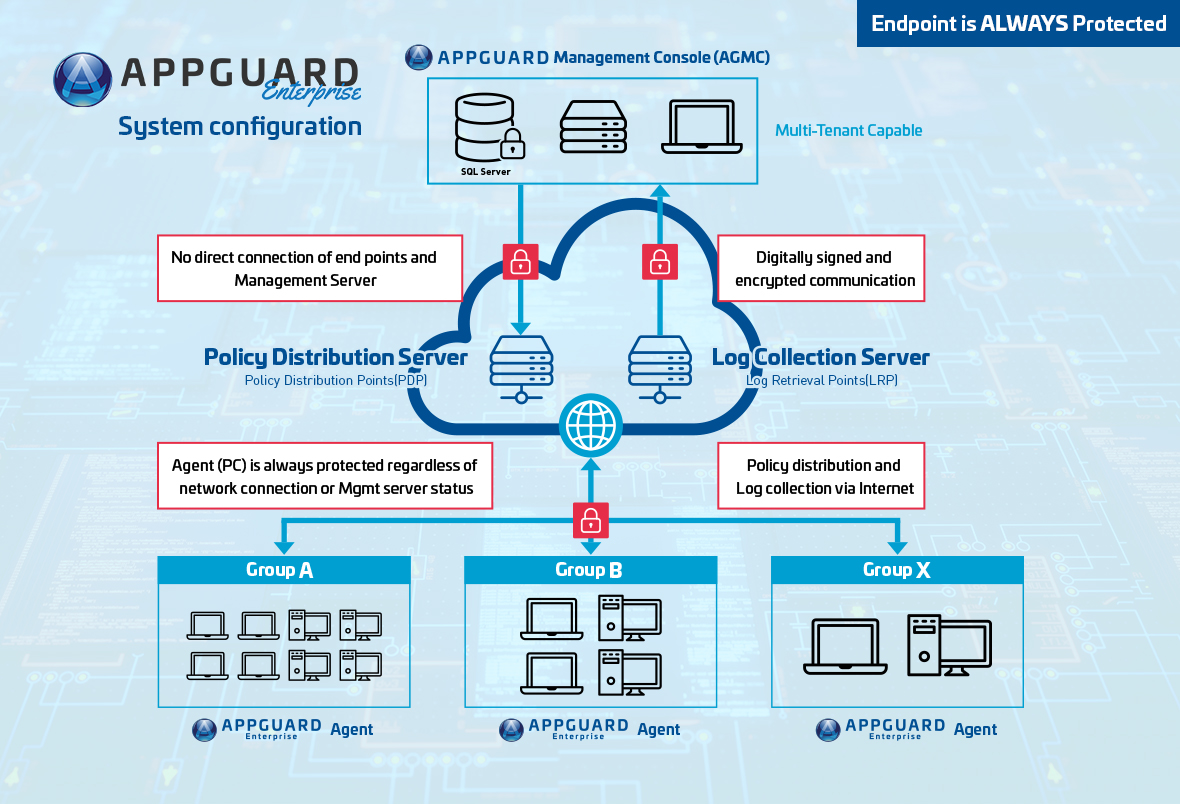
Even after you deploy a security product, the operation could be a nightmare. Updating signature files or downloading the latest AI engine, new version releases of the product… you need to verify and test before enterprise wide deployment to make sure that it does not affect your current IT environment. Also regarding operations, do you want to manage by yourself on-premise or outsource the management to AppGuard Managed Service Provider. The choice is up to you. The architecture of AppGuard Enterprise is military grade robustness with Confidentiality, Integrity, and Availability that meets the standards of the U.S. government agencies.
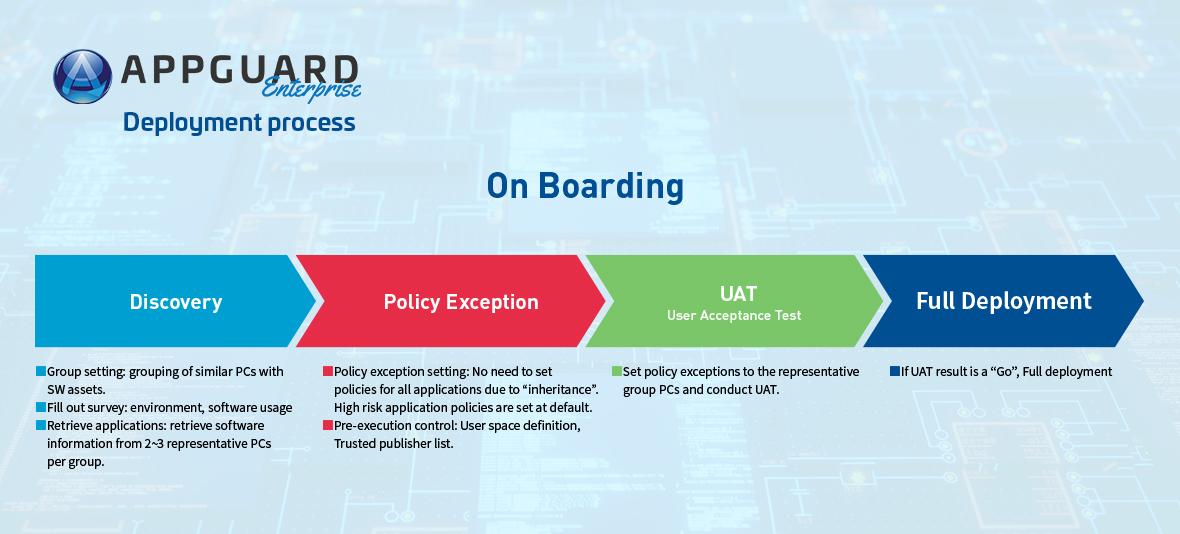
“On Boarding” process will help reflect your enterprise characteristics accurately
AppGuard’s basic concept is only launch trustworthy applications, and even after the trusted applications are launched, AppGuard will prevent any process that tries to harm the system. Each enterprise may have some differences in the definition of Trusted Applications, hence, when deploying AppGuard to an enterprise, it is important to go through the on boarding process. On Boarding is like the initial security consulting assessment while respecting the characteristics of an enterprise, it seeks to balance security risk versus convenience.
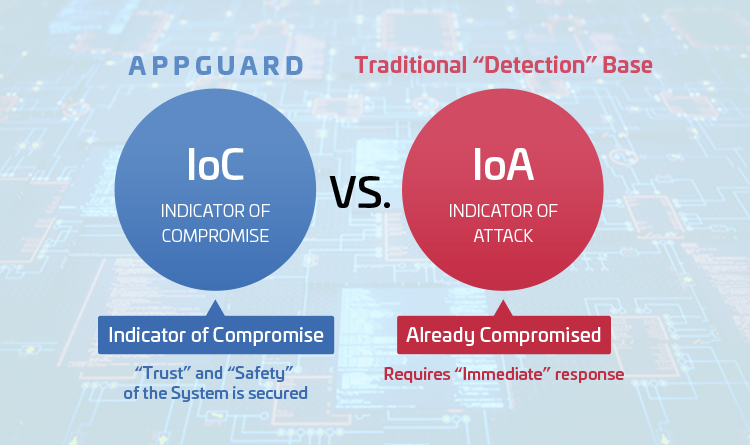
[IoC vs. IoA]:From defensive to offensive IT strategy
AppGuard's defense concept is based on Indicator of Attack (IoA) idea, by preventing the attackers from trying to accomplish. On the other hand, the concept the conventional security is considered to be Indicator of Compromise (IoC) which require immediate response during attacks or postmortem if they are not detected. Today conventional endpoint security products are more accurate by adopting new detection methods such as AI and behavior detection, but they are still based on past threats and cannot react to new threats. Therefore, countermeasures after compromise are required using monitoring services such as EDR and SOC. AppGuard blocks malicious processes and ensures system safety. Therefore, there is no need for immediate response.
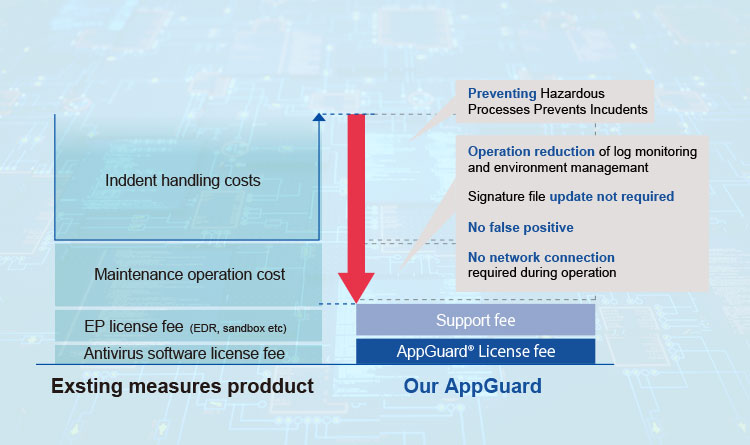
Total cost simulation
An overall picture of security costs cannot be determined solely by license fees. It is also necessary to consider the operational costs of security measures as a whole and the risk factors for incidents. AppGuard does not require periodic downloads of definition files, AI engines, etc., so there is no need for internal verification that is required each time. It protects the system from unauthorized processes, eliminating the need for 24/7 monitoring and significantly reducing personnel expense. Even for unknown threats that have been increasing in recent years, AppGuard's defense concept of “OS Protection” protects system from increasing unknown threats and it will not trouble you with ransom payments and incident costs.